Whether your wordpress is personal or business related, when you think about having a hacked site, you also immediately think of the last time you visited the site, it can be the day before, or weeks before, no matter the date, now that there are indicators that your site is hacked, the most recommended action is to be calm as there is always a solution for it.
We know that having a secure website is essential as it is your business card, you want to get customers, be discoverable in Search Engine Results and build credibility but having a hacked website is actually very common. It usually occurs when wordpress is not updated or when its plugins are not updated and hackers take advantage of it. Fortunately, as there are hackers trying to exploit vulnerabilities, there are also experts willing to work with you and deliver a protected website.
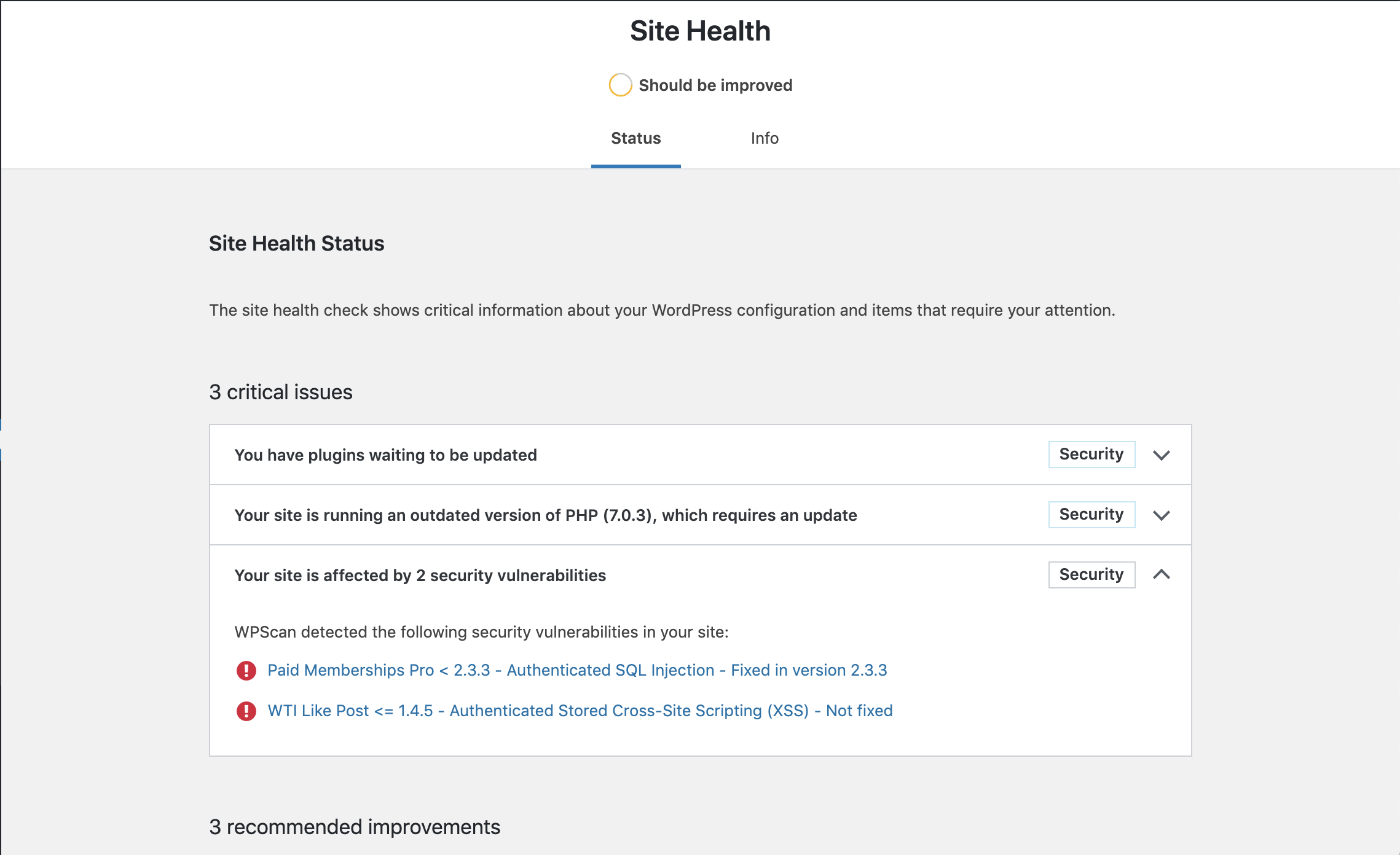
If you started noticing unusual user activity, such as creation of new users, existing users’ password changes, user role changes, unapproved new content and modification of existing content, it is very likely that the wordpress site is hacked. What you need to do next is start removing malware, spam, and other hacks, in other words, disinfection the site.
A disinfection of a wordpress website should include:
Analysis and search for threats
- Search for threats at the user level, studying the behavior of the application when accessed from different operating systems and web browsers.
- Search for threats with administrator permissions, studying the different files hosted on the server in order to find the malicious code inserted in the application
- Analysis of the threats found.
Disinfection and neutralization of the threats found
- The files affected by the malicious code should be disinfected, thus neutralizing the threats found in the previous phase.
Search for exploitation vectors
- Possible entry vectors to be analyzed for the origin of the infection
- The most common input vectors in WordPress-based applications are: o Default credentials o Insecure authentication process o Injections o Upload of malicious code through an Uploader.
Patching vulnerabilities
- A patch to be made of the vulnerabilities found.
- A set of recommendations to be made, in order to avoid future infections.
Finally an executive report should be made, highlighting findings and organizing them by the impact over the business/web application. Along with the report an executive presentation with the results should be performed in order to expose the final result and introduce improvements and future ideas.

The recommended tool to perform the wordpress disinfection is WPScan, a vulnerability scanner for WordPress. It was developed by the WPScan Team and sponsored by the renowned security company Sucuri.
As WordPress disinfection is not an easy task, it should be performed by a team of experts committed to achieve the project goals in terms of quality, deadlines and costs.
At Puffin Security, we use the ELITE SECURITY CONSULTING methodology so you can rest assured that your organization will have the highest level of security.
Complete the form, and we’ll be in touch as soon as possible




